In this article we will look at User Datagram Protocol (UDP) which is one of the famous protocols in TCP/IP protocol suite and in IoT.
What is UDP?
The User Datagram Protocol, or UDP for short, is a protocol that allows datagrams to be sent without connection in IP-based networks. To achieve the desired services on the target hosts, it uses ports that are listed as one of the core components in the UDP header. Like many other network protocols, UDP belongs to the internet protocol family, where it is classified as a mediator between the network layer and the application layer at the transport level.
UDP is a direct alternative to the more common TCP, although the two protocols differ by one point. While transmission via TCP takes place only after the obligatory three-way handshake, UDP forgoes this procedure in order to keep the transmission time as short as possible. By using the User Datagram Protocol, an application can send information very quickly, since neither a connection to the addressee has to be established nor do you have to wait for an answer.
However, there is no guarantee that packets will arrive complete and in the same order in which they were sent. In addition, the protocol does not provide its own protection against manipulation or access by third parties. However, faulty packets can be detected by an optional usable checksum (mandatory in combination with IPv6). UDP (User Datagram Protocol) is a connectionless protocol of the internet protocol family that operates at the transport layer and was specified in 1980 in RFC 768. The properties of UDP are:
- UDP is connectionless
- UDP uses ports
- UDP enables fast, delay-free communication
- UDP does not guarantee the security and integrity of the data
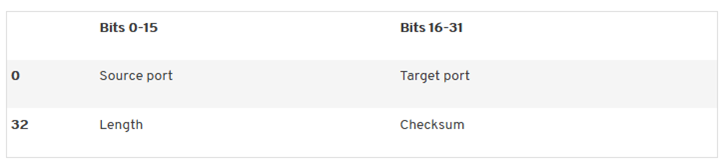
UDP Header
UDP header is as shown below.
The first 16 bits of the header area reveal the source port via which the respective data packet is sent. The receiver needs this information to be able to respond to the packet. Since UDP is connectionless and there is no exchange between addressee and receiver, this field is optional. Therefore, the value “0” is usually set here.
In the next field, the target port and thus the service to be accessed is specified. In contrast to the source port, this information is mandatory, otherwise the datagram cannot be assigned correctly. The length field defines the length of the datagram. This consists of the length of the header (8 bytes) and the size of the user data (theoretical maximum: 65,535 bytes).
The UDP header is terminated by the checksum, which is used for error detection during transmission. In this way, any manipulations of the transmitted data can be detected – however, corresponding packets are discarded without a new request. The checksum is optional in IPv4, but is used by most applications by default. If you omit it, this field will also take the value “0.” If UDP is used in combination with IPv6, the checksum is mandatory.
The User Datagram Protocol has a minimalistic structure and missing mechanisms in order to guarantee a complete, successful transmission, but cannot be used as a universal transport protocol. Rather, it was designed from the outset for applications that do not (yet) require a reliable transmission service. The field of application of UDP is consequently limited, but nevertheless underlines the enormous value of the protocol, as the following application classes for UDP prove.
- Best-effort delivery applications
- Lightweight applications
- Applications with their own mechanisms for reliable transmission
- Multicast applications
- Real-time applications (Games, Chat, etc…)

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply