In this article we will look at what is steganography and the process of encoding and decoding an object using steganography.
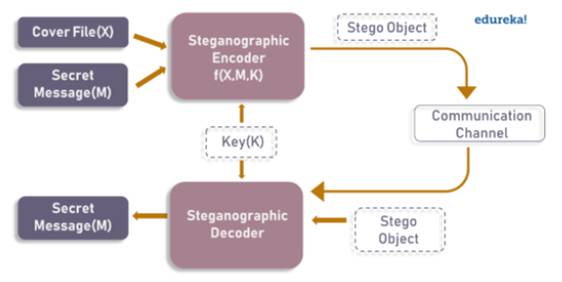
Steganography means concealed writing. It is a way of data hiding. Steganography can also be referred using different names like data hiding, information hiding, and digital watermarking. Digital watermarking can be used to detect illegal copies of the original material. The overall process of steganography can be illustrated as shown below.
Watch this video to learn about steganography:
At the sender side, the input to the steganographic encoder contains the secret message M, cover file X and an optional stego key K. The output of the encoder is a stego object which is the cover file. The encoder uses some sort of technique to embed the secret message M in the cover file X. The changes in the cover file X are negligible if the message M is short. On the receiving side, the steganographic decoder takes the input of stego object and the optional stego key K. The decoder’s output will be the cover file X and the secret message M.
The main difference between steganography and cryptography is, in cryptography the secret message is either scrambled or converted into non-human understandable form. In steganography the secret message remains same, but is hidden from plain sight.
Steganalysis is the art and science of detecting hidden messages in the cover files like images or audio or video files. The goal of steganalysis is to identify suspected bits, or bytes of data which is hidden in the cover files. Automated tools can be used to detect such hidden data in images or audio or video files.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply