In this article we will look at phishing attack in a comprehensive way. We will start with what is phishing attack, phishing using email, methods of phishing, phishing techniques, types of phishing scams and much more.
Contents
What is Phishing?
Phishing is the activity of sending genuinely seeming emails with fake links or attachments containing files embedded with virus or other malicious programs to their target user or a group of target users. The goal of phishing is in general for accessing or collecting the personal information of their targets or credit card numbers for performing financial fraud.
Watch this video to learn about basics of phishing attack:
Phishing is the use to social engineering tactics to trick users into revealing confidential or sensitive information. Phishing has become a universal phenomenon and is still a major threat in the present era. Attackers take advantage of various contemporary incidents to craft threatening or enticing messages which makes the users click fake links and provide necessary information for the attackers.
Wikipedia defines phishing as criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication.
The general steps in Phishing are:
Phishing through Email
E-mail is a popular medium used in the phishing attacks and such emails are also called as spam. However, not all emails are spam emails. It is important to understand these types of emails with which we deal every day. We will discuss about two such emails: i) Spam emails ii) Hoax emails.
Spam email
Also known as junk email, spam involves sending similar messages to numerous recipients. Spam emails have steadily grown over the years and still stays as major type of email in the Internet. Botnets, a network of infected systems spread around 80% of spam. Types of spam emails are:
Unsolicited Bulk Email (UBE): It is a synonym for spam. Unsolicited messages sent to a large number of people.
Unsolicited Commercial Email (UCE): Unsolicited messages sent to numerous people for commercial purpose, generally for advertising.
Hoax email
Hoax email may or may not be spam. Hoax email is a deliberate attempt to deceive or trick a user into believing that something is real, even though it is fake. Sometimes it is difficult to recognize whether email is spam or a hoax email.
To maximize the chances of recipient to respond to the phishing email, the phisher might use any one of the following tactics:
- Names of legitimate organizations: Phisher tries to use the name of a already well established organization and follows the look and feel of the organization’s website in the email.
- From a real employee: Phisher uses the real name of an employee working in the organization in the from field of the email. If the recipient calls the organization and asks whether the person is actually an employee in the organization, he/she will get a positive response and gets assured.
- URLs that look right: Phisher creates a duplicate of a original webpage, hosts it on a different server and sends a link to that duplicate page in the phishing email. Even though the text in the link looks legit, the underlying URL will be a fake address.
- Urgent messages: Using fear to trigger response is a common practice in phishing emails. The attacker/phisher uses sense of urgency in the email body. Some examples, might be “your account is hacked”, “your email space is filled and will deleted in 24 hrs if there is not further action”.
Different measures for reducing the spam that we receive are:
- Share personal email id with limited number of people and on few public websites
- Never reply or open any spam emails
- Don’t write your email id as it is in plain text on public websites; use images or replace @ symbol with the word “at” and replace . symbol with the word “dot” to prevent email harvesters from gathering your email id
- Never use personal or business email ids on shopping or entertainment websites
- Do not forward any emails from unknown recipients
- Make a habit of previewing an email before opening it
- Never use email id as the screen name in chat rooms
- Never respond to spam email to unsubscribe from the mail distribution list; unsubscribing actually acknowledges that it is a valid email id
Watch this video to learn in-depth about phishing techniques:
Methods of Phishing
Different methods used by phishers to entice the netizens to reveal their personal information are as follows:
Dragnet: This method involves sending enticing emails or other ways to a large number of people. The recipients perform an action like clicking a fake link which presents a duplicate page of a legitimate website. The user then enters the required information like username, password, debit card or credit card details, etc. In this method the phisher does not have a specific target in mind. Fake emails are sent to random people. This may also involve other ways of sending fake links like popups, SMS, etc.
Rod-and-Reel: In this method, phishers target specific people to reveal their confidential information like bank account details etc. This method requires phishers to perform initial reconnaissance to gather general information like targets email ids etc.
Lobsterpot: This method focuses on creating spoofed websites. The phisher creates exact duplicate of a well established legitimate website and sends links to the duplicate site disguised as legitimate links in an email or though other transmission methods. This method targets a specific individual or a group of people. Victims open the email and think that the link belongs to the legitimate website clicks it and provides the necessary information like bank account details etc. In fact the data is sent to the phisher website.
Gillnet: This method depends far less on social engineering techniques and relies on more advanced techniques like Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), etc. Attackers inject malicious code directly into the email or into the pop-ups displayed on a webpage. When the victim opens an email or clicks on a popup or visits a webpage, the malicious code will enter the victim’s system. This code can be a keylogger, virus, or a trojan that can steal sensitive information and send it to the attacker.
Phishing Techniques
The common ways used by phishers to launch phishing attacks are as follows:
- URL manipulation: Links are used in web pages and emails to direct a user to a certain webpage. Phisher use fake links to direct users to duplicate or fake web pages to gather sensitive information.
- Filter evasion: Modern browsers as well as mail services like Gmail, Hotmail, etc., provide anit-phising or anti-spam services that can detect spam or phishing emails and mark them. To avoid certain filtering mechanisms phishers might use an image instead of text link in the email.
- Website forgery: In this technique phisher creates a duplicate web site which provides similar services as a reputed website. By using techniques like cloaking, or URL redirection, the phisher sends the victims to the duplicate site for providing sensitive information.
- Flash phishing: Anti-phishing toolbars in web browsers can scan a web page and alert the user whether the page is safe or not. Phishers can use flash files to evade the detection from anti-phishing toolbars and make the user believe that the page is indeed safe.
- Social phishing: In this technique phishers entice the users to reveal sensitive data by other means as given below:
- Phisher sends an email to the victim as if it was sent from a bank asking to call them as there was a security breach
- The victim calls the bank on the phone numbers displayed in the email
- As the phone number is fake, victim gets redirected to the phisher
- Phisher imitates as a bank employee and asks the victim to provide sensitive information like bank account details
- Phisher gets the required details easily
- Phone phishing: There are techniques like mishing, smishing, and vishing using which a phisher can obtain confidential information from the victim. Also, a phisher can create fake caller ID details posing as an employee from trusted organization and access data from the victim.
Spear Phishing and Whaling
Spear phishing is a method of phishing in which the email or message is sent to specific person or group of people in a company or organization. In spear phishing, the message is sent to the victim by spoofing the sender address to imitate a fellow employee or even a higher official in the company or organization. The email might ask the victim employee or official to provide necessary information for accessing the company’s internal systems. Once the victim provides sensitive information like username and password, the attacker will use that information to further penetrate into company’s information system and steal valuable information.
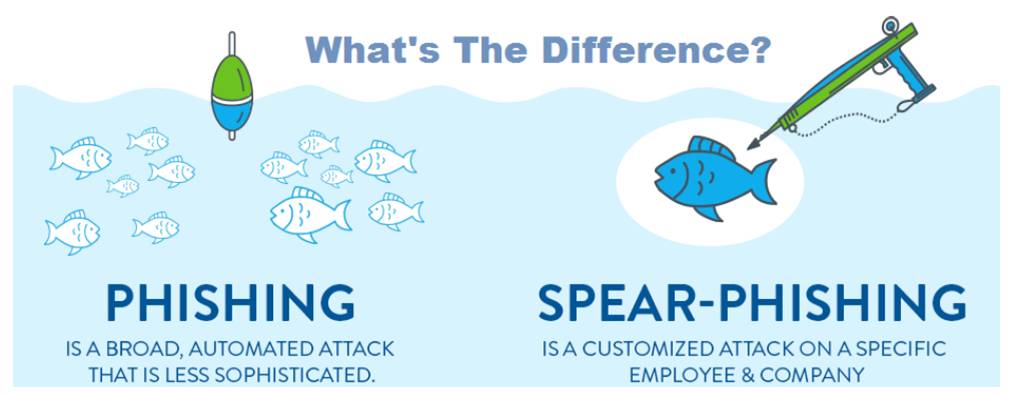
Whaling is a specific form of phishing or spear phishing. In whaling the top-level executives of a company or organization are targeted. The attacker carefully crafts a phishing email which is tailored for the executives. Once the top-level executive opens the email and provides necessary information, the details are sent to the attacker. In general, whaling emails contains keyloggers or trojans sent as attachment to the email. The difference between phishing and spear phishing is as shown in the picture below.
Types of Phishing Scams
Generally found phishing scams are as follows:
- Deceptive phishing: Phishing scams in which email messages are sent to a vast number of people with the intent of ID theft. Email messages with spoofed sender address are sent to people. The messages contain links to fake or duplicate websites in which the victims enter sensitive information.
- Malware-based phishing: In this type of phishing scam, the email messages are attached with malicious software like keylogger, trojan, or virus. Once the victim opens the mail and clicks the attachment containing malware, the software executes and steals sensitive information on the victim’s machine.
- Keyloggers: This is a special type of malware-based phishing. Victims receive email which contains keylogger as attachment disguised as legitimate files. Once the victim clicks the attachment, the keylogger gets installed on the machine and secretly monitors all the keystrokes of the victim. Periodically it sends this logged information to the attackers email or machine.
- Session hijacking: In this phishing scam victim activities are monitored by the attacker. When the victim logs in to the banking or other related websites, the attacker captures the authentication token and later reuses those authentication tokens to perform unauthorized transactions.
- In-session phishing: This phishing scam involves an attacker capturing an ongoing session between victim and a target website. A pop-up window is displayed to the victim which contains a page related to the target website. Victim thinks that the pop-up is actually a part of the target website and provides required sensitive information which stored on attacker’s machine.
- Web Trojans: It is a special type of malware-based phishing scam. The email messages contains links or attachments containing a trojan. When the victim clicks the attachment or link, the trojan infects the victim machine.
- Pharming: Pharming is a phishing scam in which the attacker redirects the victim to fake or duplicate websites. Pharming includes other techniques like hosts file poisoning and DNS phishing.
- Hosts file poisoning: A hosts file is local file in the machine which contains mappings between the domain/host name and IP address. While resolving the IP address for a given domain name, the hosts file is given the top priority. An attacker can write malicious mappings in the hosts file to redirect a victim to fake website.
- DNS phishing: DNS is a application layer protocol which translates a textual domain name to corresponding IP address. In DNS phishing or DNS hijacking, the attacker modifies the DNS information so that a victim is redirected to a website which is controlled by the attacker.
- System reconfiguration attacks: In this kind of phishing scam, attackers use various techniques to change the setting s of system. For example an attacker can turn off the firewall or anti-virus to allow access to the victim’s system. This may also involve an attacker modifying favorites file to redirect the victim to malicious sites.
- Data theft: Phishers can use various forms of phishing and other techniques to steal sensitive or confidential information from individuals or companies or organizations and sell them on black markets to make a living.
- Content-injection phishing: In this type of phishing scam, the attacker modifies the part of legitimate web page to capture sensitive information from a victim. For example, an attacker might inject malicious code to display a login form or other HTML forms in a valid webpage which makes the victim believe that the form is actually a part of the parent webpage.
- MITM phishing: This phishing involves an attacker acting as middle man between two entities. Using techniques like ARP poisoning, DNS poisoning, etc, the attacker redirects the victim to a fake website to capture his/her sensitive information.
- Search engine phishing: This scam involves attackers creating legitimate looking fake websites and ranking them in search engines by using various blackhat techniques. When the victim searches for some keywords in the search engine, the fake website will be shown in the search results. The victim clicks the link and provides sensitive information.
- SSL certificate phishing: This is an advanced type of scam in which the attackers mimic legitimate SSL certificates to imitate legitimate websites. When the victim visits a fake website whose domain is very similar to a popular domain, and sees the secure lock symbol, he/she thinks that the fake website is indeed the original popular website and provides sensitive information which is captured by the attacker.
Following are the measures for guarding against phishing scams:
- Update antivirus regularly
- Don’t click unknown hyperlinks in emails
- Use anti-spam software
- Verify https while browsing websites
- Use anti-spyware software
- Educate yourself regarding various phishing techniques and scams
- Use Microsoft Baseline Security Analyzer (MBSA) to detect various vulnerabilities in Windows operating system
- Turn on firewall
- Take backups regularly
- Don’t click and enter sensitive in unknown pop-ups
- Secure hosts file
- Protect against DNS and pharming attacks
You can visit and read the following links for more information on Phishing:

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply