In this article we will discuss the need capabilities for IoT system in general and explore necessary elements in device layer and server layer.
The five entities behind an IoT system are:
- Device platform (devices and microcontrollers)
- Software for device APIs and interfacing
- Connecting and networking protocols
- Server and application programs
- Cloud platform for storage and computing
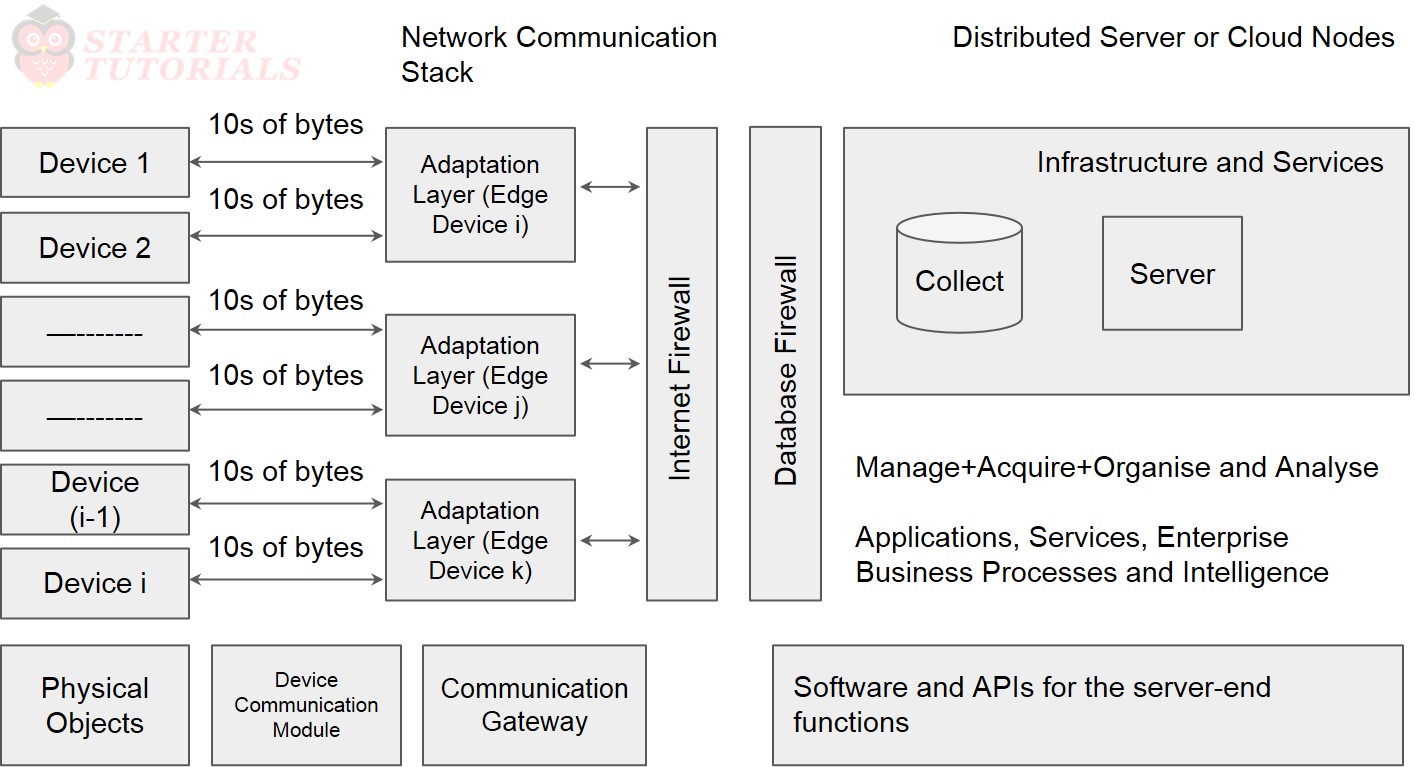
An IoT system in general can be represented using the following architecture:
Designing the device layer requires the following components:
- Design a physical object/device with device hardware consisting of microcontroller, firmware, including sensor(s), actuator(s), RFID or Wireless Sensor Node (WSN).
- Design the communication module at the device: software consisting of device APIs and device interface for communication over the network and communication circuit/port(s).
- Software for device action(s) on the message, information or commands received followed by outputs for the actuators, such as glowing LEDs, streetlights.
- Communication gateway (requires creation of communications stack)
RFID tag, is a device with wireless transceiver, powered by nearby wireless radiation energy or power source. The device communicates the object’s ID to a nearby reader, and uses Near-Field Communication (NFC) protocol. WSN is a device with a wireless transceiver that can sense the value of a physical state and communicate it with nearby devices.
IoT servers are the web servers, enterprise servers, cloud servers, data centers, databases, and application servers. Servers offer the following:
- Online platforms
- Device identification, identity management and their access management
- Data acquisition, aggregation, integration, organisation, and analysis
- Use of web applications, services and business processes

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply