In this article we will look at file permissions in Unix with examples and commands associated with managing file permissions in Unix.
Contents
Introduction
Every file has a set of permissions associated with it, which determines who can do what with the file. If your directory contains files with sensitive information, we can change their permissions such that they are not accessible to other users. Care should be taken that on every Unix system, there is a special user called super user who can read or modify any file on the system.
The special login name root carries super user privileges which is used by system administrators. There is command called su that grants the super user status if you know the root password.
For more privacy, we can change the data in the file by using the crypt command which makes the file non-readable. Although crypt command is fairly secure, it not a bullet proof solution. In real life, most security breaches are due to weak passwords.
Whenever an user is created, the system assigns a login identification (login-id), an user-id or uid (a number) and a group-id (a number). The file system determines what you can do by the permissions granted to your uid and group-id.
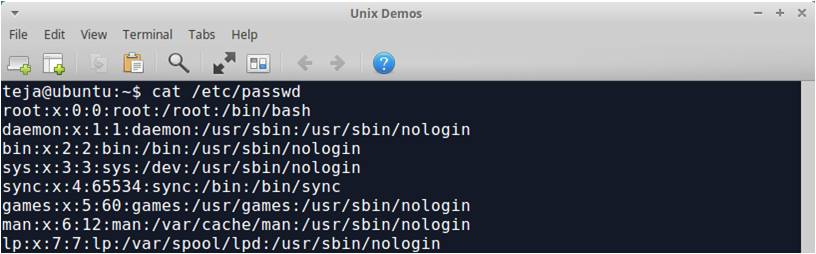
The file /etc/passwd is the Unix password file, which contains the login information of all users of that system. The general format of a line from this file is as given below:
The content of /etc/passwd file is as shown below:
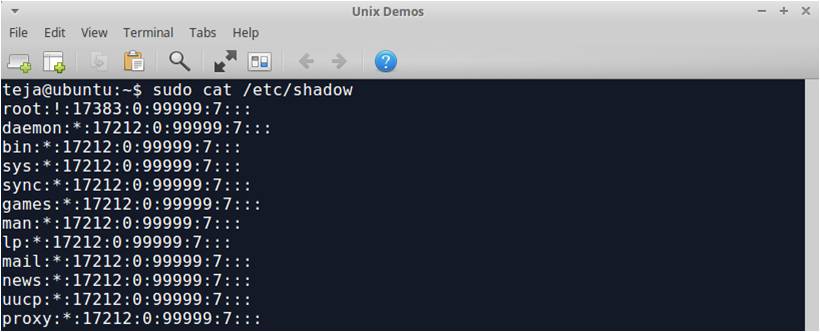
The character x in the password field says that the password is encrypted and is stored in a separate file /etc/shadow. The content of this file is shown below:
File Permissions in Unix
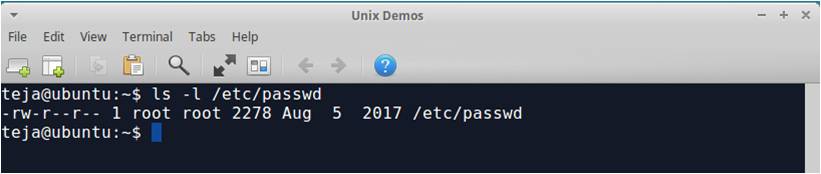
Let’s observe the permissions for the file /etc/passwd. We can see the permissions by using the command ls -l as shown below:
There are three kinds of permissions for each file: read, write, and execute. Also we can have different permissions for different people. In the figure above we can see that the file permissions are displayed as rw-r–r–.
The first three permissions belongs to the owner of the file. The second three permissions belongs to the people in the group to which the owner belongs to and the third set of three permissions belongs to the people outside the group which contains the owner. We can say that the owner (root) has read and write permissions on the file. The people in the group (root) has read permission and everyone else has read permission.
For a directory, read permission means we can use ls command to list the contents of the directory or use other commands to access the files in the directory. The write permission allows us to delete or create files in that directory. The execute permission means whether we can search for a file in that directory or not.
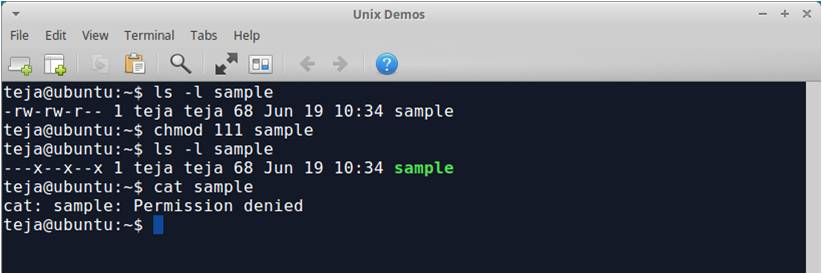
The chmod (change mode) command changes the file permissions. The permissions can be specified as octal numbers or by symbolic description. While using numbers, 4 is for read, 2 is for write, and 1 is for execution permission. The maximum value for a permission is 7 (read+write+execute) and minimum value is 1 (execute). We can use chmod commad as shown below:
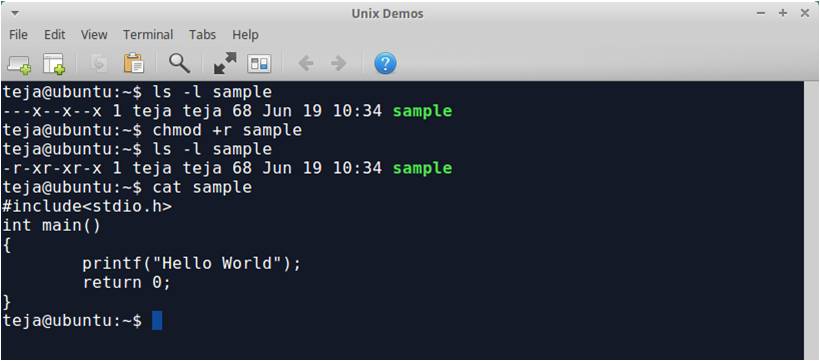
For symbolic codes we can use + sign for turning on a certain permission and – for turning off a certain permission for all users. Changing file permissions using symbolic codes is shown below:
Changing the permissions on a directory will not change its modification date. The modification date reflects the changes to files in the directory, not to the changes in permissions of the directory. The permissions and dates are not stored in the directory/file itself. They are stored in a system structure called index node (inode).
The chmod Command
This command is used to change the permissions of a file after it is created. Only the owner of the file or the super user can change file permissions. The general usage of this command is given below:
The expression can contain the following information:
- The information about the category of users (user – u, group – g, others – o, all – a).
- The information about granting, or removing the permission (+, -, =).
- The information about the type of permission (read – r, write – w, execute – x).
The + operator is used to grant permissions and the – operator is used to remove the permissions. The = operator is used to assign absolute permission i.e., when we give a permission using = operator, already existing permissions will be removed.
To assign execute permission for the owner (user) we can write chmod u+x filename. To remove write permission for group we can write chmod g-w filename. To assign read permission for all users we can either write chmod a+r filename or we can write chmod +r filename.
We can also use octal numbers for assigning permissions to a file. For read we will give 4, for write we will give 2, and for execute we will give 1. While using octal numbers we will specify a three digit number, where each digit can be a maximum of 7. For example, to assign read-write-execute to owner, read-write to group, and read to others, we can write chmod 761 filename.
The chown Command
When a file is created by a user, he/she becomes the owner of that file. Sometimes, it is required to change or transfer the ownership of a file from one user to another user. We can do so in two ways. One way is to copy the file from the current user directory to the new user’s directory. Second way is to use the chown command.
For example, to change the owner of the file myfile to the user John, we can write chown John myfile. We can also use -R option to change the ownership of all files recursively in the current directory.
The chgrp Command
We can change the group of an existing file by using the chgrp command. Only the owner of the file can change the group membership of a file. We may have to change the group when new groups are created or when files are copied to a new system.
For example, to change the group of a file myfile to the group name newgroup, we can write chgrp newgroup myfile. We can also use -R option to change the group membership of all files recursively in the current directory.
For additional information, you can visit the following links:
- How Unix file permissions work
- Manage file permissions on Unix
- How to use Unix and Linux file permissions

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply