In this article we will look at what are DoS and DDoS attacks. We will also look at the classification and types of DoS and DDoS attacks.
Contents [hide]
What are DoS and DDoS Attacks
A denial-of-service attack (DoS) or a distributed denial-of-service (DDoS) is a cyber-attack in which the hacker seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. These attacks affect the availability of the system.
Watch this video to learn about DoS and DDoS attacks:
The United States Computer Emergency Response Team defines symptoms of DoS attacks to include:
- Unusually slow network performance
- Unavailability of a certain website
- Inability to access any website
- Dramatic increase in the number of spam emails being received
The goal of DoS or DDoS attacks is not to gain unauthorized access to systems or data, but to prevent intended users of a service from using it. A DoS attack might do the following:
- Flood a network with traffic, thereby preventing legitimate network traffic
- Disrupt connections between two systems, thereby preventing access to a service
- Prevent a particular individual from accessing a service
- Disrupt service to a specific system or person
Classification of DoS and DDoS Attacks
DoS and DDoS attacks can be classified as follows:
- Bandwidth attacks: In this attack, the attacker tries to exhaust the bandwidth of a target host or website. Opening a website consumes some bandwidth in the form of text, images, etc. The attacker tries to send large number of fake web page access requests, thereby consuming the bandwidth. In some cases, the attacker might try to flood the target network or host by sending a large volume of random packets. Examples include: UDP flood, TCP flood, ICMP flood, ping flood, etc.)
- Logic attacks: In this attack, the attacker tries to exploit vulnerabilities in the network or website software such as the web server software or the TCP/IP stack. Examples of logic attacks include: buffer overflow attacks, Remode Code Execution (RCE) attacks based on the vulnerabilities in the web server software or database software.
- Protocol attacks: In this attack, the attacker tries to use a feature or bug in the implementation of the protocol to exhaust the resources on the target machine like CPU, memory, or network bandwidth. Examples include: SYN attack, Ping of Death, Smurf attack, Slowloris, etc.
- Unintentional DoS attack: This is not really an attack. It is a scenario in which a website or host (server) experiences a sudden bump in legitimate traffic and categorizes it as a DDoS attack. This kind of scenario is called a flash crowd. A website might experience a flash crowd when a larger famous site posts a story or link to a smaller unpopular website. The visitors of the larger site might follow the story or link which causes a sudden increase in traffic.
Types of DoS and DDoS Attacks
Types or levels of DoS attacks are as follows:
- Flood attack: This is the most frequent form of DoS attack. In this attack the attacker sends huge volume of packets to the victim machine making it unable to process the packets and take it offline. The sender should have more bandwidth than the victim in order to perform a flood attack. A classic example is a ping flood in which the attacker sends a huge volume of ICMP ping packets. Other examples of flood attack are TCP flood, SYN flood, UDP flood, etc.
- Ping of death attack: This attack was possible due to a bug in Berkeley implementation of TCP/IP stack. The maximum size of a packet is 65536 bytes. In this attack, the attacker sends a ICMP ping packet of size greater than the maximum size. When the target machine receives this modified or malformed packet, it is unable to process it and sometimes the machine freezes or reboots or shuts down making it unavailable. This is a old attack which doesn’t work in the modern times.
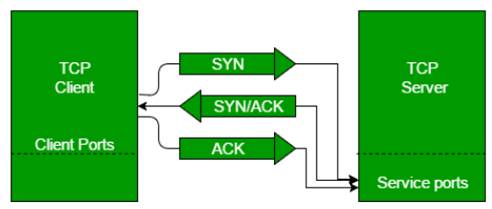
- SYN attack: This attack is also called as TCP SYN attack as it is based on the vulnerability in the handshake mechanism of Transmission Control Protocol (TCP). In the connection establishment phase of TCP, a three-way handshake is performed. First the sender sends a SYN packet to initiate the connection. The receiver responds back with a SYN+ACK packet if it is ready to communicate. Then sender sends an ACK packet acknowledging the communication from the receiver. This three-way handshake mechanism is illustrated below:
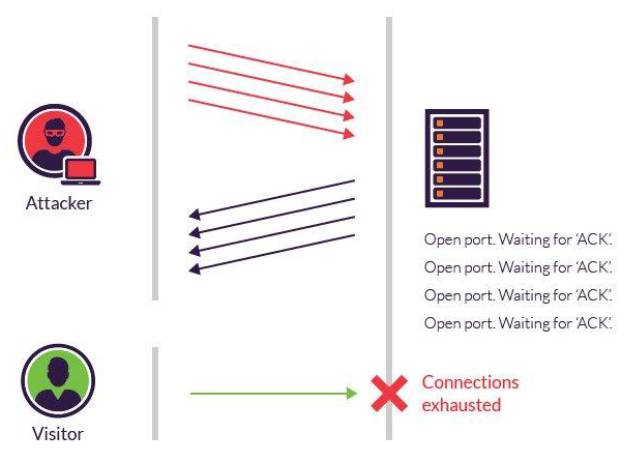
- In the SYN flood attack, the attacker sends a huge volume of SYN packets to the target host (receiver). The target host responds back with SYN+ACK packets and waits for the sender to send ACK packets. But, the attacker doesn’t send the ACK packets to the target host thereby making the
target waste the resources like buffers in the memory and CPU cycles to process the requests. This attack is illustrated below.
- Teardrop attack: In the IP header there are fields like fragment offset, total length etc, for supporting fragment reassembly at the receiver. A message coming from the higher layer (transport layer) is divided into multiple parts called fragments at IP layer. The attacker messes with the values of the before mentioned fields and makes the receiver confused while reassembling the fragments into the message. This might sometimes hand or freeze the system. This is due to the algorithm of TCP/IP fragmentation reassembly mechanism. This attack can crash hosts running operating systems like Windows 3.1x, 95, NT and some versions of Linux (prior to versions 2.0.32 and 2.1.63).
- Smurf attack: In this attack, the attacker sends an ICMP echo packet (ping) to a broadcast network address with the source IP address spoofed with target or victim machine’s IP address. If the network contains 1000 machines, all the 1000 machines will send back an ICMP echo reply (ping) back to the sender which is the IP address of the victim machine. This attack can be considered as an amplification attack in the sense that a single request is amplified into a larger number of replies flooding the victim machine.
- Nuke attack: This is a old generation DoS attack which involves an attacker sending crafted ping packets to the victim machine until it slows down or comes to a complete halt. This attack no longer works in the modern networks.
The measures which allows us from being a victim of DoS or DDoS attack are as follows:
- Implement filtering at firewall to limit certain DoS attacks
- Patch the operating system and other network software to guard against TCP SYN flood attacks
- Disable any unused or unnecessary network services
- Enable quota systems on your OS if available
- Create a baseline of the system’s resources and detect any deviations from the baseline
- Perform examination of physical security as a routine
- Use Tripwire or similar software to detect changes in configuration information or other files
- Invest is disaster recovery and continuity plans
- Invest in redundant and fault tolerant network configurations
- Establish and maintain regular backup schedules and policies
- Establish and maintain appropriate password policies especially for high privileged accounts

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply