In this article we will look at digital forensics life cycle. We will explore different phases or steps in the digital forensics life cycle.
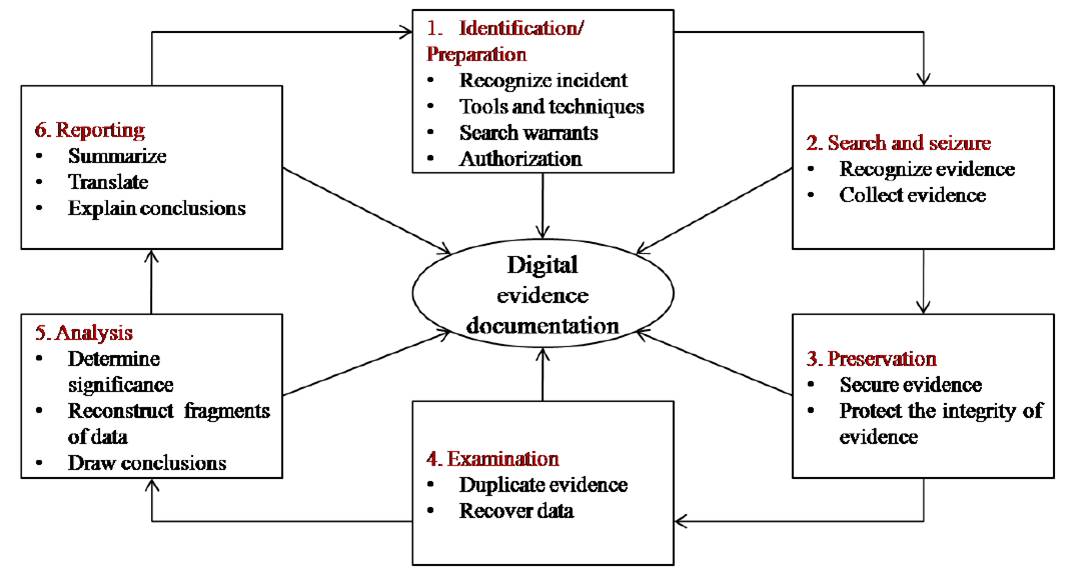
The digital forensics process is shown in the following figure. Forensic life cycle phases are:
1. Preparation and identification
2. Collection and recording
3. Storing and transporting
4. Examination/investigation
5. Analysis, interpretation, and attribution
6. Reporting
7. Testifying
Watch the below video to learn about digital forensics life cycle:
Contents
1. Preparing for the Evidence and Identifying the Evidence
In order to be processed and analysed, evidence must first be identified. It might be possible that the evidence may be overlooked and not identified at all. A sequence of events in a computer might include interactions between:
- Different files
- Files and file systems
- Processes and files
- Log files
In case of a network, the interactions can be between devices in the organization or across the globe (Internet). If the evidence is never identified as relevant, it may never be collected and processed.
2. Collecting and Recording Digital Evidence
Digital evidence can be collected from many sources. The obvious sources can be:
- Mobile phone
- Digital cameras
- Hard drives
- CDs
- USB memory devices
Non-obvious sources can be:
- Digital thermometer settings
- Black boxes inside automobiles
- RFID tags
Proper care should be taken while handling digital evidence as it can be changed easily. Once changed, the evidence cannot be analysed further. A cryptographic hash can be calculated for the evidence file and later checked if there were any changes made to the file or not. Sometimes important evidence might reside in the volatile memory. Gathering volatile data requires special technical skills.
3. Storing and Transporting Digital Evidence
Some guidelines for handling of digital evidence:
- Image computer-media using a write-blocking tool to ensure that no data is added to the suspect device
- Establish and maintain the chain of custody
- Document everything that has been done
- Only use tools and methods that have been tested and evaluated to validate their accuracy and reliability
Care should be taken that evidence does not go anywhere without properly being traced. Things that can go wrong in storage include:
- Decay over time (natural or unnatural)
- Environmental changes (direct or indirect)
- Fires
- Floods
- Loss of power to batteries and other media preserving mechanisms
Sometimes evidence must be transported from place to place either physically or through a network. Care should be taken that the evidence is not changed while in transit. Analysis is generally done on the copy of real evidence. If there is any dispute over the copy, the real can be produced in court.
4. Examining/Investigating Digital Evidence
Forensics specialist should ensure that he/she has proper legal authority to seize, copy and examine the data. As a general rule, one should not examine digital information unless one has the legal authority to do so. Forensic investigation performed on data at rest (hard disk) is called dead analysis.
Many current attacks leave no trace on the computer’s hard drive. The attacker only exploits the information in the computer’s main memory. Performing forensic investigation on main memory is called live analysis. Sometimes the decryption key might be available only in RAM. Turning off the system will erase the decryption key. The process of creating and exact duplicate of the original evidence is called imaging. Some tools which can create entire hard drive images are:
- DCFLdd
- Iximager
- Guymager
The original drive is moved to secure storage to prevent tampering. The imaging process is verified by using the SHA-1 or any other hashing algorithms.
5. Analysis, Interpretation and Attribution
In digital forensics, only a few sequences of events might produce evidence. But the possible number of sequences is very huge. The digital evidence must be analyzed to determine the type of information stored on it. Examples of forensics tools:
- Forensics Tool Kit (FTK)
- EnCase
- Scalpel (file carving tool)
- The Sleuth Kit (TSK)
- Autopsy
Forensic analysis includes the following activities:
- Manual review of data on the media
- Windows registry inspection
- Discovering and cracking passwords
- Performing keyword searches related to crime
- Extracting emails and images
Types of digital analysis:
- Media analysis
- Media management analysis
- File system analysis
- Application analysis
- Network analysis
- Image analysis
- Video analysis
6. Reporting
After the analysis is done, a report is generated. The report may be in oral form or in written form or both. The report contains all the details about the evidence in analysis, interpretation, and attribution steps. As a result of the findings in this phase, it should be possible to confirm or discard the allegations. Some of the general elements in the report are:
- Identity of the report agency
- Case identifier or submission number
- Case investigator
- Identity of the submitter
- Date of receipt
- Date of report
- Descriptive list of items submitted for examination
- Identity and signature of the examiner
- Brief description of steps taken during examination
- Results / conclusions
7. Testifying
This phase involves presentation and cross-examination of expert witnesses. An expert witness can testify in the form of:
- Testimony is based on sufficient facts or data
- Testimony is the product of reliable principles and methods
- Witness has applied principles and methods reliably to the facts of the case
Experts with inadequate knowledge are sometimes chastised by the court. Precautions to be taken when collecting digital evidence are:
- No action taken by law enforcement agencies or their agents should change the evidence
- When a person to access the original data held on a computer, the person must be competent to do so
- An audit trial or other record of all processes applied to digital evidence should be created and preserved
- The person in-charge of the investigation has overall responsibility for ensuring that the law and these are adhered to
Chain of Custody
A chain of custody is the process of validating how evidences have been gathered, tracked, and protected on the way to the court of law. Forensic professionals know that if you do not have a chain of custody, the evidence is worthless.
The chain of custody is a chronological written record of those individuals who have had custody of the evidence from its initial acquisition to its final disposition. A chain of custody begins when an evidence is collected and the chain is maintained until it is disposed off. The chain of custody assumes continuous accountability.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply