Contents
Aim
To implement flow control protocols like Sliding Window, Go Back N, and Selective Repeat protocols.
S/W required
NS2
Background information
Sliding window protocol
The working of the sliding window protocol can be divided into two steps sender steps, and the receiver steps and also some important values are needed in a network model for smooth transmission of the data frames are:
- Sender and the receiver side
- Window Size
- The total data frames to be transmitted
- Proper sequencing of the frames
Steps for the sender side
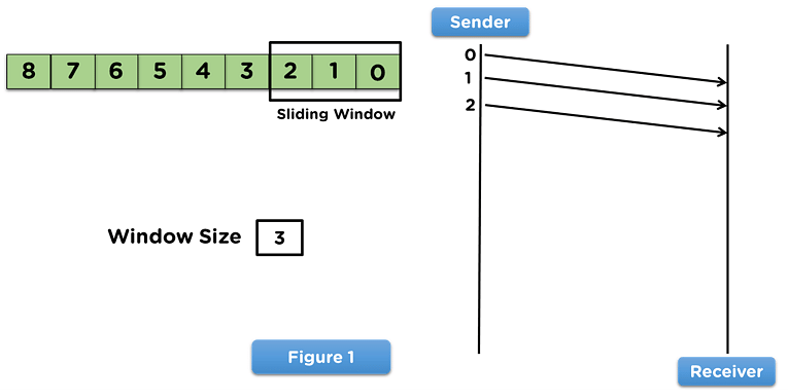
- To begin with, the sender side will share data frames with the receiver side per the window size assigned to the model.
- The sliding window will appear on the frames transmitted over to the receiver side.
- Then the sender will wait for an acknowledgment from the receiver side for the shared frames, as mentioned in below figure.
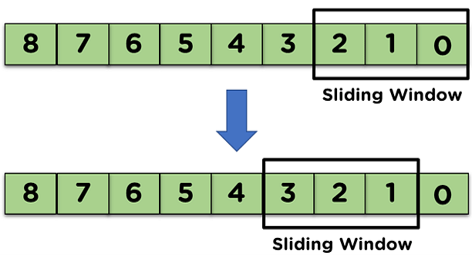
- When the receiver transmits the acknowledgment of the first transmitted frame, the sliding window will shift from the acknowledged frame.
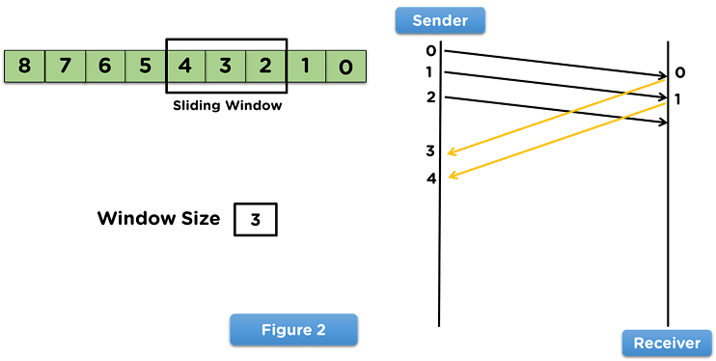
Steps for the receiver side
- On receiving the data frames from the sender side, the receiver will use the frames in the network model.
- After the receiver uses the frame, it will transmit the acknowledgement to the sender side for that data frame.
- Then, the receiver side will receive the next data frame from the sender side, as mentioned in below figure.
This process continues until all the frames are transmitted from the sender side to the receiver side, and the receiver side transmits the acknowledgment of all the received frames.
There are two types of sliding window protocols:
- Go-Back-N ARQ
- Selective Repeat ARQ
Go-Back-N ARQ
The Go-Back-N ARQ is one of the Sliding Window Protocol strategies that is used where reliable in-order delivery of the data packets is required. In the Go-Back-N ARQ, we use the concept of a timer. When the receiver receives the correct frame, it sends back an acknowledgment or ACK. Once the sender gets an ACK for a data frame, it shifts its window forward and sends the next frame. If the ACK is not received within the specified period then all the data frames starting from the lost frame are retransmitted.
In the Go-Back-N ARQ, the sender’s window size is taken as N but the receiver’s window size is always 1. Hence, the sender can send N data frames at a time but the receiver can receive only 1 frame at a time. The Go-Back-N ARQ is used for noisy channels or links and it manages the flow and error control between the sender and the receiver.
Go-Back-N is quite easy to implement but here lot of bandwidth is used in case of high error rate for the retransmission of the entire window every time.
Selective Repeat ARQ
The selective repeat ARQ is one of the Sliding Window Protocol strategies that is used where reliable in-order delivery of the data packets is required. The selective repeat ARQ is used for noisy channels or links and it manages the flow control between the sender and the receiver. In selective repeat ARQ, both sender and receiver window size is N.
In the selective repeat ARQ, we only retransmit the data frames that are damaged or lost. If any frame is lost or damaged then the receiver sends a negative acknowledgment (NACK) to the sender and if the frame is correctly received, it sends back an acknowledgment (ACK). As we only resend the selected damaged frames so we name this technique the Selective Repeat ARQ technique. The ACK and the NACK have the sequence number of the frame that helps the sender to identify the lost frame.
Activity
Program
#Implmentation of Go-Back-N protocol
#Create Simulator Object
set ns [new Simulator]
#Initialization code
set namfile [open out.nam w]
$ns namtrace-all $namfile
#Termination code
proc finish {} {
global ns namfile
$ns flush-trace
close $namfile
puts "Executing NAM..."
exec nam out.nam &
exit 0
}
#Creating nodes
set n1 [$ns node]
set n2 [$ns node]
#Assign labels to nodes
$ns at 0.0 "$n1 label Sender"
$ns at 0.0 "$n2 label Receiver"
#Creating links
$ns duplex-link $n1 $n2 10Mb 10ms DropTail
#Setting queue limit
$ns queue-limit $n1 $n2 10
#Creating TCP agent and TCP sink
set tcp [new Agent/TCP]
$ns attach-agent $n1 $tcp
set sink [new Agent/TCPSink]
$ns attach-agent $n2 $sink
#Connect TCP agent and TCP sink
$ns connect $tcp $sink
#Creating FTP application
set ftp [new Application/FTP]
$ftp attach-agent $tcp
#Setting TCP window size and congestion window size
#window_ is the upper bound on the advertised window for the TCP connection.
$tcp set window_ 4
#maxcwnd_ is the upper bound on the congestion window for the TCP connection.
$tcp set maxcwnd_ 4
#Set the location of node labels
$ns at 0.0 "$n1 label-at up"
$ns at 0.0 "$n1 color Red"
$ns at 0.0 "$n2 label-at up"
$ns at 0.0 "$n2 color Blue"
#Set the timing of events
$ns at 0.3 "$ftp start"
$ns at 2.8 "$ftp stop"
$ns at 3.0 "finish"
$ns run
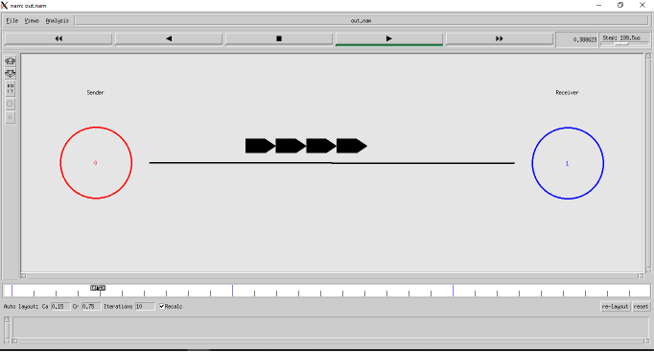
Input and ouput
Result
Sliding window, Go Back N, and Selective Repeat protocols were understood and implemented successfully.
References
Visit DCCN lab programs for more study material.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply