The consensus algorithms in blockchain can be classified into two broad categories:
- Traditional—voting-based consensus
- Lottery-based—Nakamoto and post-Nakamoto consensus
Traditional voting-based consensus has been researched in distributed systems for many decades. Algorithms like Paxos and PBFT are prime examples of such types of algorithms.
Traditional consensus can also be called fault-tolerant distributed consensus. In other words, this is a class of consensus algorithms that existed before Bitcoin.
Lottery-based or Nakamoto-type consensus was first introduced with Bitcoin. This class can also be simply called blockchain consensus.
The fundamental requirements of consensus algorithms boil down to safety and liveness conditions. A consensus algorithm must be able to satisfy the safety and liveness properties.
Safety: This requirement generally means that nothing bad happens. There are usually three properties within this class of requirements, which are listed as follows:
- The agreement property requires that no two processes decide on different values.
- Validity states that if a process has decided a value, that value must have been proposed by a process. In other words, the decided value is always proposed by an honest process and has not been created out of thin air.
- A process must decide only once.
Liveness: This requirement generally means that something good eventually happens.
- This liveness property states that each honest node must eventually decide on a value.
Contents
Proof-of-Work (PoW)
This is a proof that enough computational resources have been spent in order to build a valid block. PoW is based on the idea that a random node is selected every time to create a new block.
The following equation sums up the PoW requirement in bitcoin:
H ( N || P_hash || Tx || Tx || . . . Tx) < Target
Where N is a nonce, P_hash is a hash of the previous block, Tx represents transactions in the block, and Target is the target network difficulty value.
This means that the hash of the previously mentioned concatenated fields should be less than the target hash value.
The only way to find this nonce is the brute force method. Once a certain pattern of a certain number of zeroes is met by a miner, the block is immediately broadcasted and accepted by other miners.
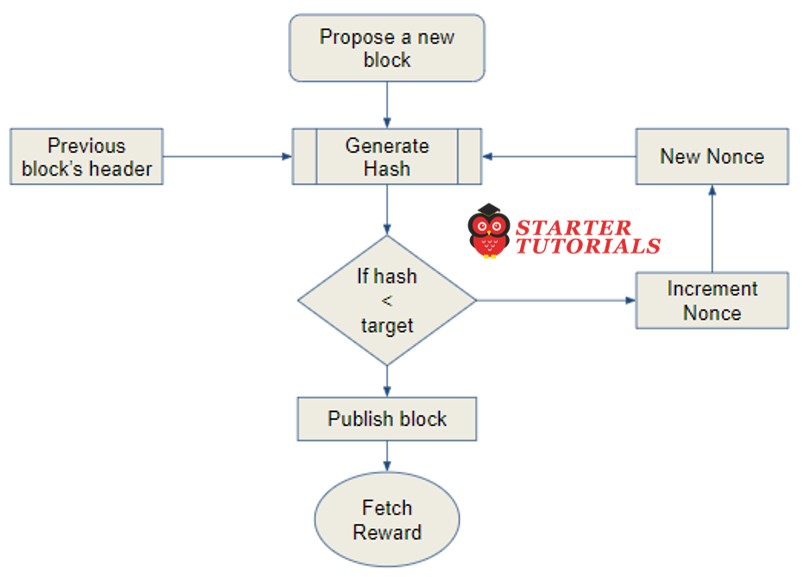
The mining algorithm consists of the following steps:
- The previous block’s header is retrieved from the bitcoin network.
- Assemble a set of transactions broadcasted on the network into a block to be proposed.
- Compute the double hash of the previous block’s header combined with a nonce and the newly proposed block using the SHA-256 algorithm.
- Check if the resultant hash is lower than the current difficulty level (target) then PoW is solved. As a result of successful PoW the discovered block is broadcasted to the network and miners fetch the reward.
- If the resultant hash is not less than the current difficulty level (target), then repeat the process after incrementing the nonce.
The above process can be visualized by using the following flowchart:
Mining difficulty increased over time and bitcoins that could be mined by single CPU laptop computers now require dedicated mining centers to solve the hash puzzle.
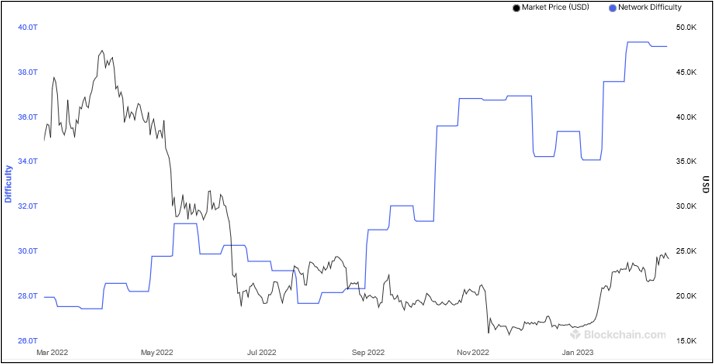
This number represents the difficulty level of the Bitcoin network. All successfully mined blocks must contain a hash that is less than this target number.
This number is updated every 2 weeks or 2016 blocks to ensure that on average 10-minute block generation time is maintained.
Bitcoin network difficulty has increased exponentially, the following graph shows this difficulty level over a period of one year:
The reason why mining difficulty increases is because in Bitcoin, the block generation time has to be always around 10 minutes.
This means that if blocks are being mined too quickly by fast hardware then the difficulty increases so that the block generation time can remain at roughly 10 minutes per block.
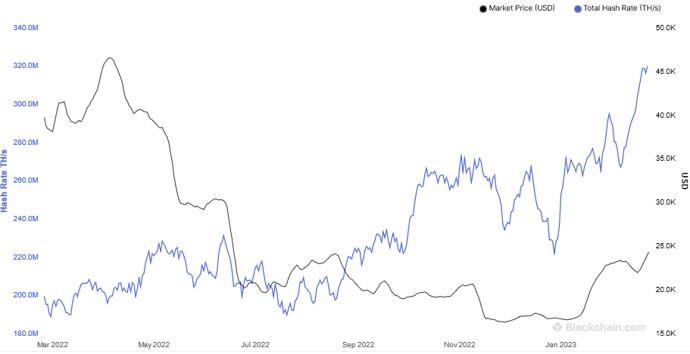
The hashing rate basically represents the rate of calculating hashes per second. In other words, this is the speed at which miners in the Bitcoin network are calculating hashes to find a block. In the early days of bitcoin, it used to be quite small as CPUs were used.
However, with dedicated mining pools and ASICs now, this has gone up exponentially in the last few years.
This has resulted in increased difficulty of the Bitcoin network. The following hash rate graph shows the hash rate increase over time.
Mining Systems
Over time, bitcoin miners have used various methods to mine bitcoins. As the core principle behind mining is based on the double SHA-256 algorithm, overtime experts have developed sophisticated systems to calculate the hash faster and faster. The following is a review of the different types of mining methods used in bitcoin and how they evolved with time.
CPU
CPU mining was the first type of mining available in the original bitcoin client. Users could even use laptop or desktop computers to mine bitcoins.
CPU mining is no longer profitable and now more advanced mining methods such as ASIC-based mining is used.
GPU
Due to the increased difficulty of the bitcoin network and the general tendency of finding faster methods to mine, miners started to use GPUs or graphics cards available in PCs to perform mining.
GPUs support faster and parallelized calculations. This turned out to be a faster option as compared to CPUs.
Users also used techniques such as overclocking to gain maximum benefit of the GPU power. GPU mining, however, has some limitations, such as overheating and the requirement for specialized motherboards and extra hardware to house multiple graphics cards.
FPGA
Even GPU mining did not last long, and soon miners found another way to perform mining using FPGAs.
Field Programmable Gate Array (FPGA) is basically an integrated circuit that can be programmed to perform specific operations.
FPGAs are usually programmed in Hardware Description Languages (HDLs), such as Verilog and VHDL.
FPGA offered much better performance as compared to GPUs; however, issues such as accessibility, programming difficulty, and the requirement for specialized knowledge to program and configure FPGAs resulted in a short life of the FPGA era for bitcoin mining.
ASICs
Application Specific Integrated Circuit (ASIC) was designed to perform the SHA-256 operation.
These special chips were sold by various manufacturers and offered a very high hashing rate. This worked for some time, but due to the quickly increasing mining difficulty level, single-unit ASICs are no longer profitable.
Currently, mining is out of the reach of individuals as vast amounts of energy and money is needed to be spent in order to build a profitable mining platform.
Now professional mining centers using thousands of ASIC units in parallel are offering mining contracts to users to perform mining on their behalf.
Mining Pools
A mining pool forms when a group of miners work together to mine a block.
The pool manager receives the coinbase transaction if the block is successfully mined, which is then responsible for distributing the reward to the group of miners who invested resources to mine the block.
This is profitable as compared to solo mining.
There are various models that a mining pool manager can use to pay to the miners, such as the Pay Per Share (PPS) model and the proportional model.
In the PPS model, the mining pool manager pays a flat fee to all miners who participated in the mining exercise, whereas in the proportional model, the share is calculated based on the amount of computing resources spent to solve the hash puzzle.
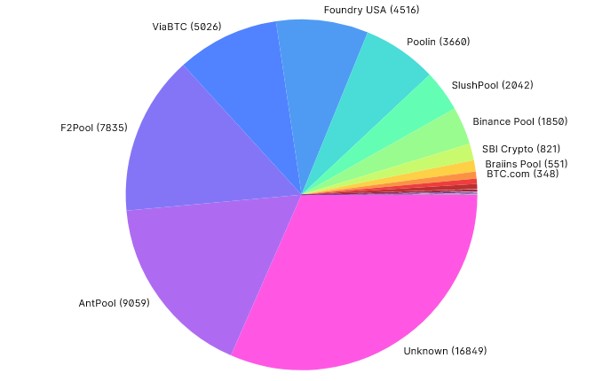
A comparison of hashing power for all major mining pools is shown in the following diagram:
Mining centralization can occur if a pool manages to control more than 51% of the network by generating more than 51% hash rate of the Bitcoin network.
A 51% attack can result in successful double-spending attacks, and it can impact consensus and in fact impose another version of transaction history on the Bitcoin network.
Theoretical solutions, such as two-phase PoW, have been proposed in academia to disincentivize large mining pools.
This scheme introduces a second cryptographic puzzle that results in mining pools to either reveal their private keys or provide a considerable portion of the hash rate of their mining pool, thus reducing the overall hash rate of the pool.
Proof of Stake (PoS)
Proof-of-stake (PoS) is the underlying consensus mechanism in Ethereum.
Ethereum switched on its proof-of-stake mechanism in 2022 because it is more secure, less energy-intensive, and better for implementing new scaling solutions compared to the previous proof-of-work architecture.
What is Proof of Stake?
In proof-of-work, miners prove they have capital at risk by expending energy. Ethereum uses proof-of-stake, where validators explicitly stake capital in the form of ETH into a smart contract on Ethereum.
This staked ETH then acts as collateral that can be destroyed if the validator behaves dishonestly or lazily.
The validator is then responsible for checking that new blocks propagated over the network are valid and occasionally creating and propagating new blocks themselves.
Proof-of-stake comes with a number of improvements to the now-deprecated proof-of-work system:
- better energy efficiency – there is no need to use lots of energy on proof-of-work computations
- lower barriers to entry, reduced hardware requirements – there is no need for elite hardware to stand a chance of creating new blocks
- reduced centralization risk – proof-of-stake should lead to more nodes securing the network
- because of the low energy requirement less ETH issuance is required to incentivize participation
- economic penalties for misbehavior make 51% style attacks exponentially more costly for an attacker compared to proof-of-work
- the community can resort to social recovery of an honest chain if a 51% attack were to overcome the crypto-economic defenses.
Validators
To participate as a validator, a user must deposit 32 ETH into the deposit contract and run three separate pieces of software: an execution client, a consensus client, and a validator.
On depositing their ETH, the user joins an activation queue that limits the rate of new validators joining the network. Once activated, validators receive new blocks from peers on the Ethereum network.
The transactions delivered in the block are re-executed, and the block signature is checked to ensure the block is valid.
The validator then sends a vote (called an attestation) in favor of that block across the network.
How a Transaction is Executed in Proof of Stake?
Following steps are involved in running a transaction using Ethereum’s PoS:
- A user creates and signs a transaction with their private key. The user defines the amount of gas that they are prepared to pay as a tip to a validator to encourage them to include the transaction in a block.
- The transaction is submitted to an Ethereum execution client which verifies its validity. This means ensuring that the sender has enough ETH to fulfill the transaction and they have signed it with the correct key.
- If the transaction is valid, the execution client adds it to its local mempool (list of pending transactions) and also broadcasts it to other nodes over the execution layer gossip network.
- One of the nodes on the network is the block proposer for the current slot, having previously been selected pseudo-randomly using RANDAO. This node is responsible for building and broadcasting the next block (beacon block) to be added to the Ethereum blockchain and updating the global state.
- Other nodes receive the new beacon block on the consensus layer gossip network. They pass it to their execution client where the transactions are re-executed locally to ensure the proposed state change is valid. The validator client then attests that the block is valid and is the logical next block. The block is added to the local database in each node that attests to it.
References
Proof of Burn (PoB)
Proof of Burn in the blockchain is a consensus algorithm that allows miners to add their block by sending some of their coins to an unspendable account.
What is Proof of Burn?
In the Proof of Burn (PoB) algorithm, miners reach a consensus by burning the coins. It’s a process in which crypto coins get permanently eliminated from regular circulation.
In such cases, the burning of coins mechanism is used to validate transactions. Hence, the more coins a miner burns, the higher the chances of adding the block to the network.
In comparison to the proof of Work (PoW) system, PoB reduces energy consumption. Moreover, compared with proof of stake (PoS) systems, PoB doesn’t need miners to stake coins to add a new block to the network.
Here, the concept of “burning the coins” means investing the native coins in virtual mining rigs (mining powers).
It allows miners with the most virtual mining rigs or a miner who invested the most coins – to add his new block of transactions to the network.
Hence, the number of burnt coins shows miners’ commitment to the network.
How does Proof of Burn Work?
Initially the miners transfer some amount of coins to an unspendable address or an escrow account.
These publicly verified unspendable accounts are randomly created with no private keys associated.
Once coins get received by burn address/accounts, it becomes useless and inaccessible.
Eventually, the burnt coins in the account are used for strengthening the security of the network.
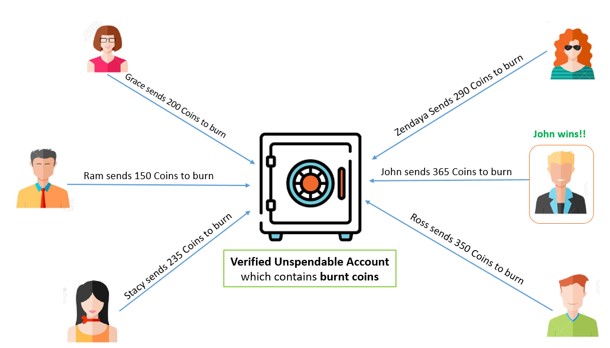
Let’s take an example to understand the working of proof of Burn (PoB). We have 6 miners, each having their own block of transactions.
As per the process, the miners have to burn some amount of coins to get an opportunity to add their block to the network.
See the below diagram. Each miner sends some of their coins to the burn address or unspendable escrow account.
John wins as he burns the maximum number of coins. Hence, he gets the chance to add his block of transactions to the network.
Moreover, the block added by John will be verified by other network validators. If the block is found invalid, then the second-highest (Ross) gets the chance to add a new block.
Proof of Burn in blockchain promotes the periodic burning of coins to avoid partiality among new and old network participants.
It means the virtual power of mining reduces each time a new block gets mined.
Moreover, it motivates miners to make regular transactions instead of just one-time investments.
Benefits of PoB
Following are the advantages of Proof of Burn in blockchain:
- Less power and energy consumption
- Motivates miners to make regular transactions using cryptocurrency
- PoB is more sustainable and doesn’t need hardware for heavy computation
- Used for long-term commitments
Limitations of PoB
Following are the disadvantages of Proof of Burn in blockchain:
- It’s not an initial consensus algorithm. It requires a number of wealthy participants to burn their coins in the network.
- PoB has not been proven to be applied on massive networks.
- It takes more time to validate the block of transactions. Hence, a bit slower mechanism.
References
Proof of Elapsed Time (PoET)
PoET is the algorithm behind Hyperledger permissioned blockchain network for businesses.
What is Proof of Elapsed Time (PoET)?
PoET is a consensus algorithm used in a permissioned blockchain network to decide mining rights and next block miner.
A permissioned blockchain network requires participants to prove their identity, whether or not they are allowed to join.
Hence, it needs permission (or invitation) to join the decentralized network as a new participant (or node).
The PoET algorithm was developed by Intel Corporation, the processor chip giant, in early 2016.
Intel is associated with the Linux Foundation in the development of Hyperledger Sawtooth. They aimed to build a highly scalable private blockchain network.
Intel introduced PoET as a time-lottery-based consensus algorithm secured by cryptography. The concept basically motivates the ideology of giving equal chances of getting a reward like a lottery.
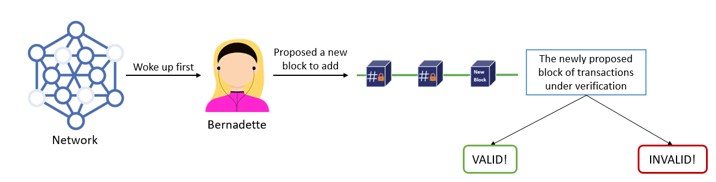
PoET Mechanism assigns an amount of time to each node in the network randomly.
The node must sleep or do another task for that random wait time. Whichever node gets the shortest waiting time wakes up and adds their block to the network.
Later, the new update information floods among other network participants.
The Proof of Elapsed time in blockchain needs to ensure 3 significant factors for this process to work:
- Ensure that the node or network participant gets the random waiting time indeed.
- Check if they are not choosing the shortest waiting time on purpose.
- Verify if the node has completed the given waiting time or not.
How does the PoET Algorithm Work?
Selection Process
- First, each participating node has to share its certificate by Intel Software Guard Extension (SGX), which ensures its validity to generate a new block in the network. After that, they are eligible to get a timer object.
- The numbers assigned to each node as a timer object (waiting countdown time) by Intel’s random number generation instruction, RAND. It generates difficult to detect random numbers.
- Now, the time object given to each participating node activates.
Generation Process
- After the time object ends and the node wakes up, it’s eligible to forge a new block to the network.
- The active node generates the hash (using a hash function like SHA-256) of its block of transactions and submits it for acceptance. It doesn’t require showing computation work done by the node.
- Afterward, the update gets flooded to the network.
Therefore, ends the iteration of mining a new block in a permissioned blockchain network using the PoET consensus mechanism.
Proof of Work (PoW) demands computation work from nodes (or miners) to become eligible for adding a new block.
On the other hand, PoET randomly selects the among participating nodes by distributing waiting time objects. Here, each node is equally eligible to mine a new block.
PoET is way more time and energy-efficient than PoW. It is backed by one of the renowned technology giants, Intel corporation, which makes it more trusting and reliable.
Benefits of PoET
Following are the advantages of the PoET consensus mechanism:
- PoET can go up to a million transactions per second.
- It is highly energy-efficient and easily scalable.
- PoET is for privately controlled spaces like business organizations.
- It ensures the same opportunity for network participants with time object and activation.
- As it’s a permissioned blockchain network, the process of selecting validators ensures network security against cyber attacks.
Limitations of PoET
Following are the disadvantages of the PoET consensus mechanism:
- PoET is a permissioned and closed network, unlike Bitcoin and Ethereum.
- The mechanism highly depends on tools by Intel technology which might raise compatibility issues with other tools later.
References
Proof of Activity (PoA)
PoA mechanism ensures that all blocks of transactions added to the network are genuine and valid.
It’s a way that helps miners to get network agreement (or consensus) to add their new block. Moreover, PoA protects the blockchain network against external and internal attacks.
What is Proof of Activity (PoA)?
Proof of Activity combines proof of work (PoW) and proof of Stake (PoS) mechanism.
First, PoA uses the mining concept by proof of work, where miners have to do complex mathematical computations to prove their efforts and sincerity to the network.
However, instead of mining a block of transactions, PoA allows miners to mine (or add) a blank template block with header information and mining reward address.
Once this almost empty block gets mined, the mechanism switches to Proof of Stake (PoS).
Then a group of validators is picked at random. They are responsible for validating or signing the new block.
Validators analyze the header information of the block and then mark it as valid or invalid.
This process continues until a block receives the required number of validators (or signers).
The higher coins the network participant holds, the stronger are their chances of being picked up as a validator (or signer).
Once the group of validators signs the new block by the miners, it’s marked as a valid, complete block and gets added to the blockchain network.
Finally, the transactions will get recorded on the newly added block.
At last, the mining fees/rewards are distributed among the miners and the group of validators who contributed to the mining process.
How does PoA Algorithm Work?
Following are the steps to the PoA algorithm:
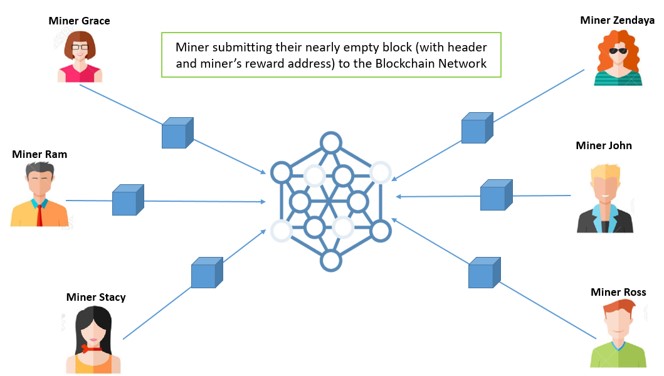
STEP 1: Process of Mining the Block (by Miners)
Miners try to submit their almost empty block (with header information and miner’s reward address) by solving a complex mathematical puzzle (finding the correct nonce and block hash)—similar to PoW.
Once the miners submit their nearly blank blocks, the consensus approach switches from PoW to the PoS mechanism.
STEP 2: Process of Signing the Block (by Validators)
This step uses the concepts of the Proof of Stake (PoS) mechanism for using network validators. However, here validators and miners are separate entities.
A group of network participants called validators (or signers) verifies the block submitted by the miners.
These network validators are selected based on their coins in the network.
The higher the coins held by a validator, have the maximum chances of getting their signed block chosen.
STEP 3: Adding transactions
Once a block gets signed by the required number of validators. It marks a valid and complete block.
Afterward, new transactions from the transaction pool add to the block. Finally, the block gets added to the blockchain network.
The mining reward is distributed among the winning block’s miner and the validators for their contribution to the network.
Benefits of PoA
Following are the advantages of the Proof of Activity mechanism:
- PoA combines to utilize PoW’s hashing system and PoS’s digital signing.
- It highly reduces the probability of a 51% attack on the network.
- Maintains the difficulty level to protect the network.
- PoA has high fault tolerance as the whole system will never shut down completely.
- Provide earning opportunities to both miners and network validators.
Limitations of PoA
Following are the disadvantages of the Proof of Activity mechanism:
- High energy consumption for mining blocks.
- Due to massive computation, the mining process takes a lot of time.
- Requires expensive hardware for computation.
- The number of validators could be less due to a lack of interest.
References

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.

Leave a Reply